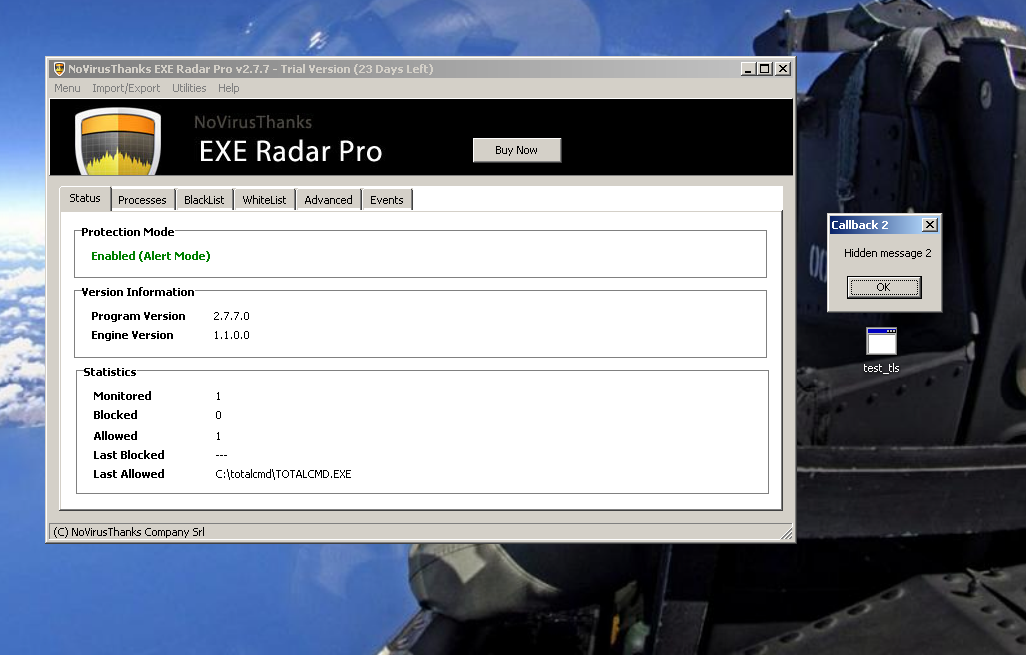
- Use Thread Local Storage callbacks, which were not blocked, to run arbitrary code.
- Masquerade as a white-listed library to execute code past the filters.
- Execute 16-bit executables, which were not blocked or registered by the ERP application filters.
1 TLS Callbacks
1.1 Description
Processes and ThreadsAn application consists of one or more processes. A process is an executing program. One or more threads run in the context of the process. A thread is the basic unit to which the operating system allocates processor time. A thread can execute any part of the process code, including parts currently being executed by another thread.
Thread Local Storage
All threads of a process share its virtual address space. The local variables of a function are unique to each thread that runs the function. However, the static and global variables are shared by all threads in the process. Thread local storage (TLS) enables multiple threads of the same process to use a global index allocated by the TlsAlloc function to store and retrieve a value that is local and unique to each thread.
TLS Callbacks
The TLS area can also be used to store code. Functions can be defined per thread that will be called before execution. When Windows loads the binary into memory, if there is any code defined in TLS it will execute it, before starting executing instructions from main entry point of the executable.
Detect
We can use PEview to inspect the TLS Directory, locate in the .DATA section:
1.2 Bypass
There is no simple official way of programatically create TLS callbacks. Nynaeve's tutorial on compiling and linking support for TLS reveals important details. The compiler and linker use a variable of type IMAGE_TLS_DIRECTORY (declared in tlssup.c) that is statically linked into every program to represent the TLS directory. The TLS directory is part of the PE header of an executable. The linker looks for a variable by the name of _tls_used and ensures that in the on-disk image, it overlaps with the actual TLS directory in the final image. More information regarding the members of the IMAGE_TLS_DIRECTORY structure are available online.The created program will register two TLS callbacks. The second one calls ExitProcess() at the end, so the code of the main() function is actually never executed
The program will execute the code in the two TLS callbacks and exit, without being detected:
2 Whitelisted NVCPL.DLL
2.1 Description
The default whitelist contains a section with allowed command lines. The first command string allowed to run is specified like this:rundll32 NVCPL.DLL,NvCplHandleHotplugEvents *
NVCPL is the NVidia driver. The syntax for rundll32 is:
> Rundll32.exe DLL_NAME,Entry_Point Optional_Argument
Parameters:
DLL_NAME - If DLL_NAME is not specified with full path, Rundll32 will search for it in the directories defined in the %PATH% environment variable. To ensure the correct DLL is called, it’s recommended to specify it in full path.
Entry_Point - The name of the exported function, that’s to be called by Rundll32.exe.
Optional Argument - Non-compulsory parameters to be passed to the function.
2.2 Bypass
We can create a DLL with the same name in the current folder, with a function named “NvCplHandleHotplugEvents”. In case the NVIDIA driver doesn't exist, the function from our crafted DLL will be called. We can then execute code without being blocked by ERP, by using the same command line mentioned in the whitelist:This event is listed as a whitelisted command being run:
3 16 bit .COM executables
3.1 Description
COM files are a type of executables. The .COM executable has no header and contains only code and data. It lacks relocation information and it is loaded by the operating system at a pre-set address, at offset 0100h. Support for legacy DOS and 16-bit Windows programs is available in 32-bit versions of Windows through NTVDM (Virtual DOS Machine).3.2 Bypass
It is possible to run a .com executable without being detected by ERP. Some tests revealed that NTVDM.exe was registered as an allowed process in the events list. The following simple executable prints a message and exits without even being registered in the events list:The source code for the demos can be found here.
Time-line
08/09/2013 - Vendor notified about TLS Callbacks vulnerability
09/09/2013 - Vendor acknowledged TLS Callbacks issue
09/09/2013 - TLS Callbacks issue is addressed in a new beta version - 3.0
16/09/2013 - Vendor notified about NVCPL library issue and 16-bi COM files code execution
19/09/2013 - Vendor acknowledged the previous 2 issues. These are reported as corrected in 3.0 version which will be released
References
A Quick Look At TLS Callbacks
R4ndoms Tutorial #23: TLS Callbacks
Thread Local Storage, part 3: Compiler and linker support for implicit TLS
Thread Local Storage - MSDN
COM file - Wikipedia
Virtual DOS Machine - Wikipedia